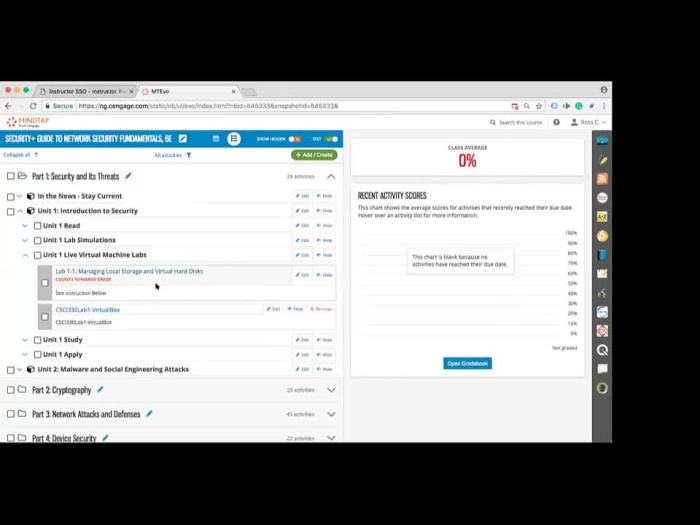
Live virtual machine lab 3.2 module 03 determining security vulnerabilities – Live Virtual Machine Lab 3.2 Module 03: Determining Security Vulnerabilities delves into the critical realm of cybersecurity, equipping you with the knowledge and skills to identify and mitigate vulnerabilities that threaten your virtual infrastructure. This module provides a comprehensive understanding of vulnerability assessment techniques, hands-on practice in executing vulnerability scans, and strategies for mitigating identified risks.
Through real-world examples and industry-standard reporting formats, you will gain the proficiency to safeguard your virtual machines and protect your organization from potential cyberattacks.
In this module, you will master the art of vulnerability assessment, employing a range of techniques to uncover potential weaknesses in your virtual machines. You will learn to differentiate between various assessment methods, understanding their strengths and limitations. The module also emphasizes the importance of vulnerability mitigation, providing practical guidance on implementing effective strategies in real-world environments.
Lab Overview
This lab provides a comprehensive approach to identifying and mitigating security vulnerabilities in live virtual machines (VMs). It is designed for cybersecurity professionals responsible for securing IT infrastructure and ensuring compliance with industry standards.
To successfully complete this lab, participants should have a fundamental understanding of VM technologies, networking concepts, and vulnerability assessment methodologies.
Vulnerability Assessment Techniques
The lab utilizes a range of vulnerability assessment techniques, including:
- Network scanning
- Vulnerability scanning
- Penetration testing
- Static code analysis
- Dynamic analysis
Each technique has its own strengths and limitations, and the lab provides guidance on selecting the appropriate technique for different scenarios.
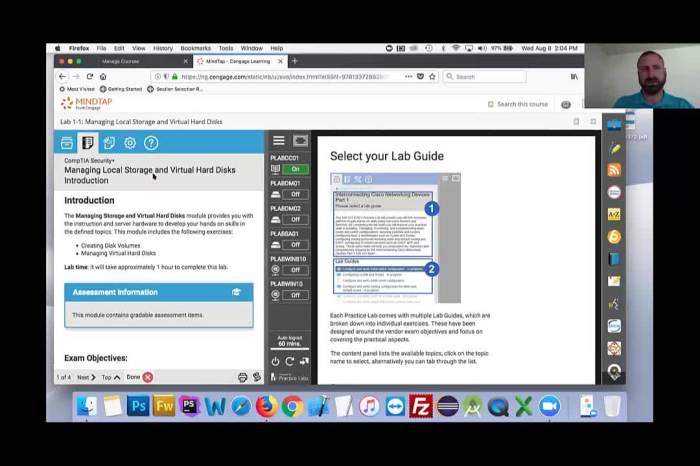
Hands-on Practice
The lab includes step-by-step instructions for setting up the lab environment and executing vulnerability assessment scans using different tools. Participants will learn how to:
- Install and configure the necessary software
- Create and deploy a target VM
- Perform network scans to identify open ports and services
- Conduct vulnerability scans to detect known vulnerabilities
- Execute penetration tests to exploit identified vulnerabilities
Mitigation Strategies
The lab emphasizes the importance of vulnerability mitigation and provides a table comparing different strategies, including:
- Patching and updating software
- Implementing security configurations
- Deploying firewalls and intrusion detection systems
- Implementing network segmentation
- Educating users on security best practices
Reporting and Communication
The lab covers the significance of effective vulnerability reporting and demonstrates how to generate a vulnerability report using industry-standard formats. Participants will learn:
- The key elements of a vulnerability report
- How to communicate vulnerability information to stakeholders
- The importance of vulnerability management and tracking
Case Studies and Real-World Examples
The lab includes real-world examples of security vulnerabilities that have been exploited in the past, such as:
- Heartbleed
- Log4j
- SolarWinds
Participants will analyze how the techniques covered in the lab can be used to prevent or mitigate similar vulnerabilities.
FAQs: Live Virtual Machine Lab 3.2 Module 03 Determining Security Vulnerabilities
What are the prerequisites for completing this module?
To successfully complete this module, you should have a basic understanding of virtualization concepts, operating systems, and networking principles.
What tools will be used for vulnerability assessment in this module?
This module utilizes a range of industry-standard vulnerability assessment tools, including Nessus, OpenVAS, and Wireshark.
How can I mitigate the security vulnerabilities identified in this module?
The module provides detailed guidance on implementing various vulnerability mitigation strategies, such as patching, configuration hardening, and network segmentation.